The Control Freak's guide to Zoom
Top 10 compliance and security controls for Zoom
Zoom CIS Benchmark
We have been doing a ton of operational work lately in order to achieve our SOC2 certification. One of the things our team automated was compliance scans for various cloud service configurations. The Zoom CIS benchmark was especially challenging. We decided to open source it for others to leverage and build upon: https://hub.steampipe.io/mods/turbot/zoom_compliance
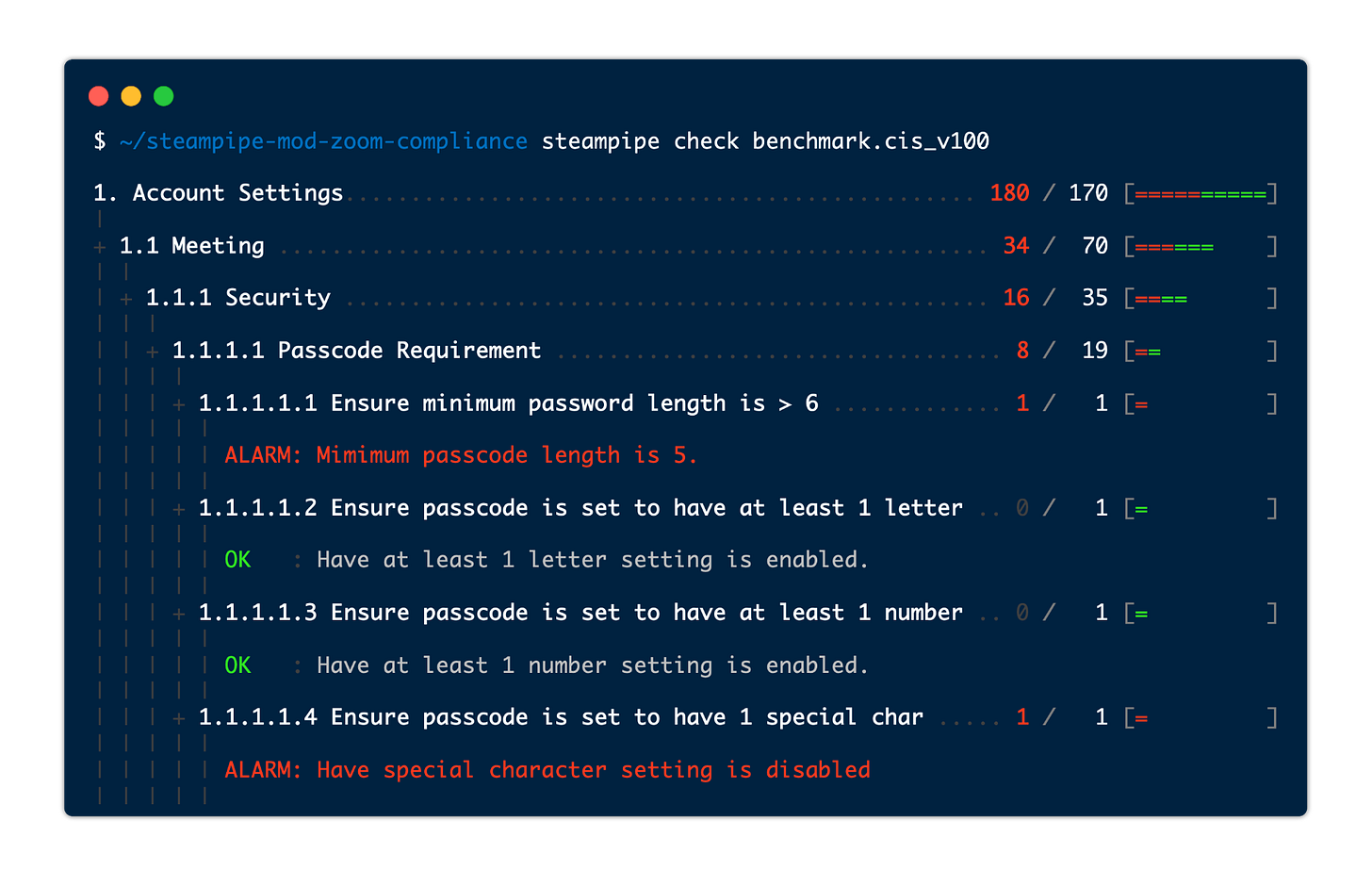
You can run the scan from your local desktop using a recently released feature of Steampipe called mods. There are currently compliance mods for AWS, Azure, GCP and Zoom built by the open source Steampipe community. The output of the mod looks like this:
The compliance mod includes the full CIS benchmark for Zoom (100+ automated checks). I thought it might be helpful to channel David Letterman and boil it down to the 10 most important controls that should be monitored, burt first a shameless plug:
If you’re intrigued the idea of building automated governance controls using SQL, I will be doing a talk at the AWS Fest 2021 on June 22nd.
I will be discussing the pros and cons of industry benchmarks vs custom controls, and doing a demo and some live coding to show how easy it is to get started.
Top 10 Zoom Governance Controls
One of the most important things to understand with Zoom is that meeting hosts have tremendous autonomy in managing meeting settings. Many governance controls in Zoom simply change default settings, but allow host to override them. For the settings in this list we recommend that you ensure the settings are ‘locked’ in your organizations configuration so only administrators can change them.
1. Require use of passcodes and passwords
Ensure the organization's account settings require passcodes.
Require a passcode for personal meetings — A common exploit across conferencing platforms is the reuse of an individual's personal meeting. Requiring a passcode to join a personal meeting can reduce the likelihood of 3rd party reuse.
Require password for participants joining by phone — To prevent unauthorized third parties from joining scheduled meetings via phone, this setting will require meeting attendees that join by phone to authenticate with a personal passcode.
Require passcode to access shared cloud recordings — If you allow hosts to share cloud recordings of their meetings, use this setting to require a password to view/download the recording.
2. Ensure adequate passcode & password complexity
There are multiple use cases within Zoom for usage of passcode/password secrets. Each has independent settings for ensuring appropriate complexity rules.
Meeting passcodes: — Meeting passcodes are distinct from user passwords, they are a shared secret that indicates the user has been invited to a specific meeting. This key control prevents unwanted attendees from guessing meeting IDs and entering meetings they weren't invited to (a.k.a. Zoom bombing).
Given that passcodes frequently show up in meeting invites, and that calendars are often visible/shared within an organization, we recommend that complexity factors be set high to encourage use of random meeting passcodes and prevent use of a meaningful pass phrases that might be a used in a password reuse attack.
Recording download passcodes — If your organization allows sharing of cloud hosted meeting recordings, those downloads should be secured by a complex random password.
User passwords — Most organizations will want to enforce single sign-on for Zoom users. With single sign-on enabled, the only users with passwords should be break-glass users and administrators with elevated access. Ensure that your user password complexity factors meets your organizations requirement for administrative secrets.
3. Ensure only authenticated users can join meetings
Ensure meeting hosts are not able to create publicly accessible meetings.
4. Enforce use of waiting rooms
Waiting rooms give hosts the ability to screen users before allowing them into a meeting. This setting can prevent unintended sharing of sensitive information (e.g. an unexpected user entering the meeting while sensitive content is being shared).
5. Prevent content sharing
Prevent exfiltration of sensitive information by limiting how hosts and users can share content.
Ensure screen capture of messaging is set to disabled — Check that settings prevent users from taking screenshots of direct messages or group conversations.
Display "Zoom Meeting" in place of meeting subject — Hosts can inadvertently disclose private information in a meeting title (e.g. A patient's name in a health care setting or an acquisition target as part of a M&A). This setting replaces the meeting title with "Zoom Meeting" so the actual meeting title isn't visble to anyone looking over the shoulder of an attendee (think of a crowded Starbucks).
Closed captioning: Ensure save captions is set to disabled — Zoom has a closed captioning feature which is likely enabled (and important) for users with hearing impairment. This setting prevents the resulting "transcript" from being saved which could be both a way to exfiltrate data and a potential legal discovery issue for the organization.
6. Enable watermarking features
Zoom’s watermarking features add "invisible" digital data to images, video and audio within Zoom that can be used in an investigation to identify a user who inappropriately shared private or sensitive information outside your organization.
7. Add timestamps to recordings
Ensures that timestamps are added to recordings to help with forensic investigation of any security/data loss incidents.
8. Ensure only local regions are enabled
Many organizations have data sovereignty requirements that require that company information and PII of customers and employees do not leave specific regions. Check these settings to ensure that only specific local regions are used when hosting your Zoom meetings.
9. Notify host when a meeting is scheduled
If someone were to compromise a host account, this setting would at least ensure that the host will be notified if an unauthorized 3rd party scheduled a meeting using their account.
10. Ensure only approved integrations are enabled
Ensure that the organization specifically reviews and approves any available 3rd party integrations before allowing them to be activated by Zoom users.
References:
Steampipe Zoom Compliance Mod — Turbot
CIS Benchmark for Zoom — CIS
Zoom Security Features — Cornell IT